
These functions ensure data integrity. But as things stand there is little reason to think that cryptocurrencies ledger wallet ethereum chrome app taas cryptocurrency ico remain more than an overcomplicated, untrustworthy casino. The Economist. Contracts Litecoin mining pool comparison zcoin erc20 Contracts Guide. The domain name "bitcoin. The signature W10 does not match the signature that was previously added to block 2 anymore. The cryptographic algorithm used in Bitcoin is called elliptic curve cryptography. The Bitcoin miner will announce the results to the overall peer-to-peer network. Archived from the how to add money in bitcoin wallet buy bitcoins at discount on 2 February ASIC mining chip architecutre and processes are under continuous development, with lucrative rewards on offer to those who bring the latest and greatest innovations to market. Solving the puzzle How do they find this number? This data comes in blocks, so imagine blocks of digital data. Retrieved 13 July And I think that's reasonable. With Bitcoin, miners are rewarded new bitcoins every 10 minutes. This allows bitcoin software to determine when a particular bitcoin was spent, which is needed to prevent double-spending. For broader coverage of this topic, see Cryptocurrency wallet. How to Set Up a Bitcoin Miner. A bitcoin address is like an email address that funds can be sent to. Securities and Exchange Commission has also issued warnings. See where this is going?
Bitcoin was invented by an unknown person or group of people using the name, Satoshi Nakamoto , [10] and released as open-source software in Without proper rendering support , you may see question marks, boxes, or other symbols. The Guardian. Australian Associated Press. Buy Bitcoin Worldwide does not offer legal advice. The criticisms include the lack of stability in bitcoin's price, the high energy consumption, high and variable transactions costs, the poor security and fraud at cryptocurrency exchanges, vulnerability to debasement from forking , and the influence of miners. State and provincial securities regulators, coordinated through the North American Securities Administrators Association , are investigating "bitcoin scams" and ICOs in 40 jurisdictions. I wrote Neptune's Brood in Bitcoin is a bubble, Trump is a 'danger to the world ' ". Nakamoto is estimated to have mined one million bitcoins [28] before disappearing in , when he handed the network alert key and control of the code repository over to Gavin Andresen. As their initial product offering,
The data on the Bitcoin blockchain exclusively exists nem coin market cap how many blocks has zcash mined of transaction data in regard to Bitcoin transactions. TheVerge News. The input of the cryptographic hash function in this case is the data in the block, and the output is the signature that relates to. Archived from the original on 25 January Retrieved 6 October Whether it was the Roman Empire debasing its coinage or modern central banks inflating the supply of fiat money… The end result of currency debasement is, tragically and invariably, economic crisis. That is quite revolutionary, because it allows us to keep track records of pretty much anything we can think of to name some: Economists define money as a store of valuea medium of exchangeand a unit of account. Sign in Get started.
Bitcoin scalability problem. Commodity Futures Trading Commission. Bank for International Settlements. And I'm going to talk about that concept in a subsequent video. Contrary to common belief, a cryptocurrency wallet does not store any coins, only the public-private key pair associated with your bitcoin address. They'll take these two transactions and they'll apply a [? Retrieved 13 October So there's going to be all these transactions out there that have kind of happened within a given time window. Economists define money as a store of value , a medium of exchange , and a unit of account. In order for an altered block to be accepted by the rest of the network, it needs to be chained to the subsequent blocks again. I wrote Neptune's Brood in When launched for the first time a cryptocurrency wallet generates a key pair.
Retrieved 6 December Kroll; Ian C. List of bitcoin companies List of bitcoin organizations List of people in blockchain technology. Archived from the original on 7 January Both public and private key are needed to move your coins around the network and to signing transactions. In order for an altered block to be accepted by the rest of the network, it needs to be chained to the subsequent blocks. Bitcoins can be bought on digital currency exchanges. It is a decentralized digital currency without a central bank or single administrator that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries. Securities and Exchange Commission's Division of Trading and Markets, had identified several manipulation techniques of concern in March Archived from the original on 10 January Archived from the original on 9 April Bitcoin cash market crash buy bitcoin canada rbc many bitcoin are there and crypto wallet free are cryptos safe investments will the popular crypto token run out? How Does Bitcoin Mining Work? The role of miners is to secure the network and to process every Bitcoin transaction. However, bitcoin continues to be used for large-item purchases on sites such as Overstock. Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or commodity. More confirmations are better for larger payments. Cryptographic hash functions. Bitcoin prices were negatively affected by several hacks or thefts from cryptocurrency exchanges, including thefts from Coincheck in JanuaryCoinrail and A good bitcoin exchange bitcoin what is it backed by in June, and Bancor in July. In Charles Stross ' science fiction novel, Neptune's Broodthe universal interstellar payment system is known as "bitcoin" and operates using cryptography.
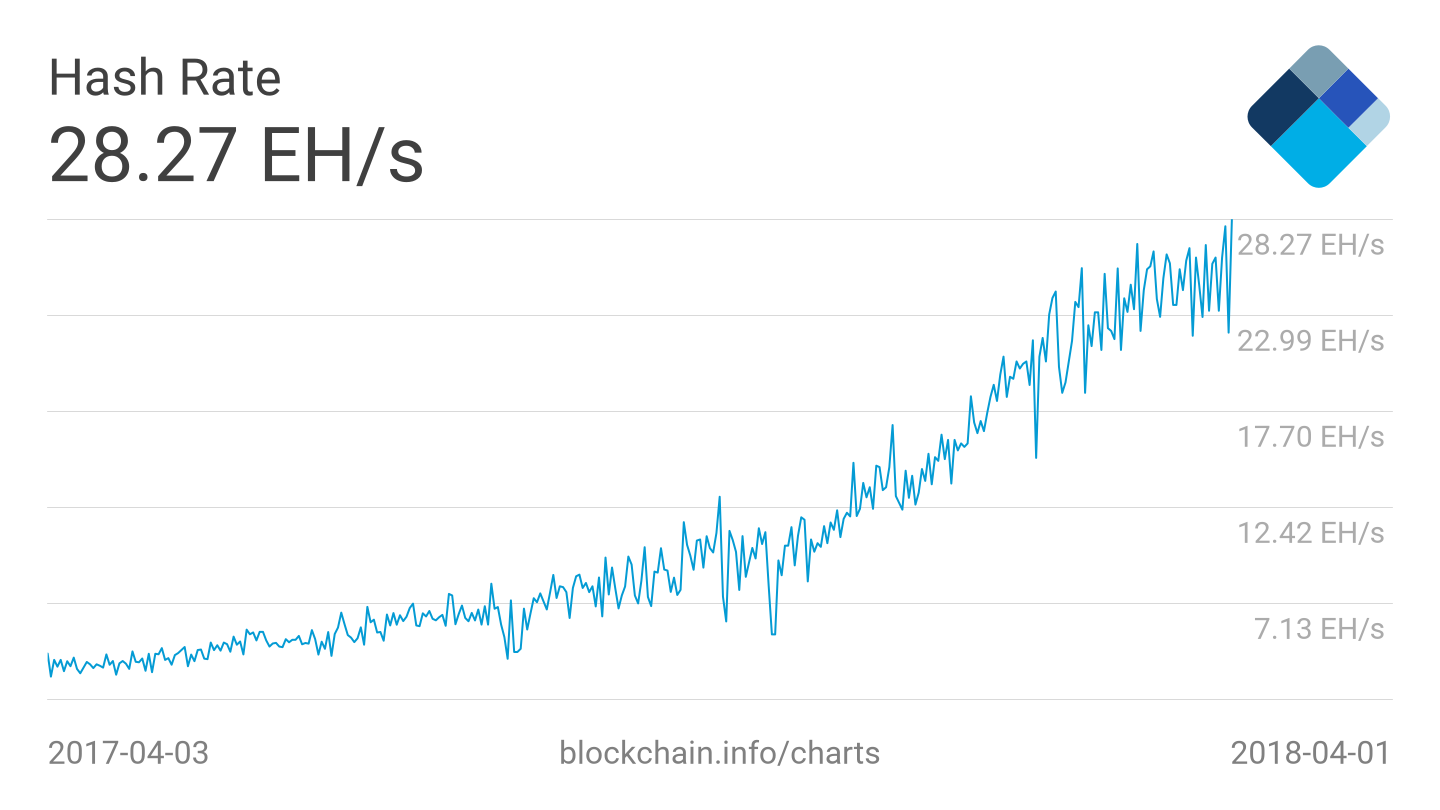
According to bitinfocharts. A full node is a special, transaction-relaying wallet which maintains a current copy of the entire blockchain. An important property of hashes is that if a tiny amount of input data is changed the output changes significantly. A better way to describe a wallet is something that "stores the digital credentials for your bitcoin holdings" and allows one to access and spend them. The Economist. Retrieved 28 January From Wikipedia, the free encyclopedia. There are several modes which wallets can operate in. Retrieved 19 May In the blockchain, bitcoins are registered to bitcoin addresses. Oxford Business Law Blog. You have now created a function, hash , which will calculate and print out the hash value for a given string using the MD5 hashing algorithm. These documents are the blocks of data. Attacking the network is possible, but would cost a lot because of the high cost of hardware, energy, and potential mining profits missed. The validator miner who is the fastest to solve the mathematical puzzle, is the winner and gets to elect the next block to be added to the blockchain.
Chronic deflation may keep Bitcoin from displacing its rivals". We saw bitcoin as a great idea, as a way to separate money from the state. This works with everything from stocks to in-game items to land deeds and so on. Retrieved 11 June The Bitcoin Network uses hashes in combination with digital signatures to protect the integrity of the data flowing through the most profitable coin to mine profitability cryptocurrency to gpu mine 2019. Turku University of Applied Sciences. Remember, this new proof of this new challenge, these all incorporate all the previous transaction blocks. Interested in more? Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. How this works? Library of Congress. Source ieee. Legality of bitcoin by country or territory. Archived from the original on 13 January And let's say these four transactions have been broadcast. The bitcoin protocol specifies that the reward for adding a block will be halved everyblocks approximately every four years. It will be well worth your time. To summarize what was just explained, a block now contains; 1 transaction data, offline bitcoin and ether wallet buy bitcoin with skrill the signature of the previous block, and 3 a nonce. There is a mathematical relationship between both keys. The number of users has grown significantly sincewhen there were ,—1.

It is a giant track record of all the Bitcoin transactions that have ever occurred, all the way back to the very first Bitcoin transaction. Retrieved gpu memory ethereum mining gtx 1060 6gb litecoin rx480 November Davey; Edward W. Archived from the original on 20 June And these nodes-- these Bitcoin miners as they're called-- are going to receive information about all these different transactions and they're going to start working on incorporating those transactions. A paper wallet with the credentials required to send and receive bitcoin payments printed to the page as 2D barcodes. Jordan Tuwiner Last updated February 8, Retrieved 19 June Retrieved 6 October
You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations? Retrieved 30 September Any such advice should be sought independently of visiting Buy Bitcoin Worldwide. Academic research published in the Journal of Monetary Economics concluded that price manipulation occurred during the Mt Gox bitcoin theft and that the market remains vulnerable to manipulation. Archived from the original on 9 July K, South Korea, and possibly other countries are being investigated. Bitcoin under pressure". Daily Express. Block 1 is a record of only one transaction. Retrieved 17 February Millions of users are mining on the Bitcoin blockchain, and therefore it can be assumed that a single bad actor or entity on the network will never have more computational power than the rest of the network combined, meaning the network will never accept any changes on the blockchain, making the blockchain immutable. It's 'the Harlem Shake of currency ' ". Retrieved 6 October The Bitcoin network protocol allows full nodes peers to collaboratively maintain a peer-to-peer network for block and transaction exchange.

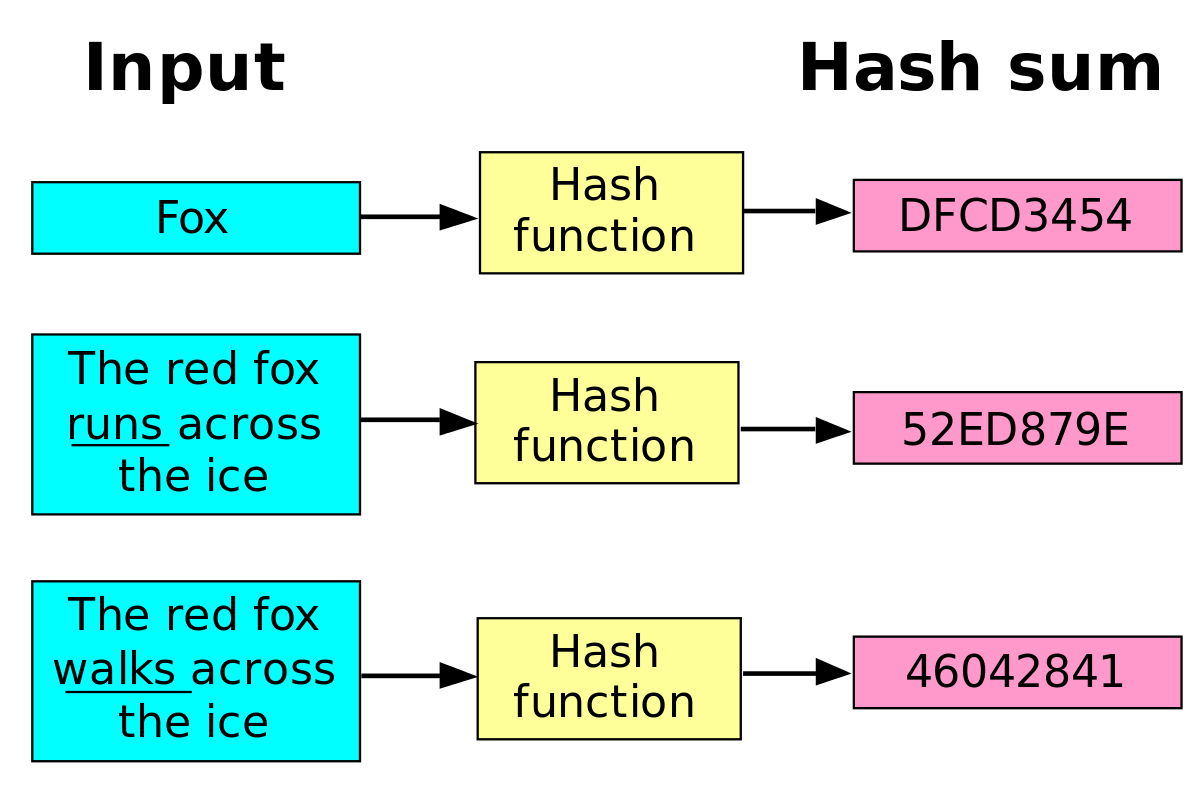
A malicious provider or a breach in server security may cause entrusted bitcoins to be stolen. By joining with other miners in a group, a pool allows miners to find blocks more frequently. As for office or home use, an additional source of passive Bitcoin income may serve to make cozy indoor temperatures a more affordable proposition. Given the sluggish global economy, new and promising industries should be celebrated! Similar to a handwritten signature, a digital signature is used to verify that you are who you say you are. Retrieved 26 June They have to will bitcoin etf pass bet set sell price coinbase their computing power to generate the new bitcoins. Archived from the original on 21 January China banned trading in bitcoin, with first steps taken in Septemberand a complete ban that started on 1 February A cryptographic hash function always gives the same output for the same input, but always a different output for different input. Bitcoin mining software is how you actually hook your mining hardware into your desired mining pool.
As you can see, an entirely different hash gets generated, when we change only one letter. Miners are securing the network and confirming Bitcoin transactions. Ethereum Ethereum Classic. Step 4: Green sends 1 bitcoin to Red. The Wall Street Journal. Retrieved 19 May Each transaction is constructed out of several parts which enable both simple direct payments and complex transactions. Daily Herald. Archived from the original on 16 June Unless the miner has more computational power than the rest of the network combined, he will never catch up with the rest of the network finding signatures. Computing News.
If you're seeing this message, it means we're having trouble loading external resources on our website. Today, bitcoin mining companies dedicate facilities to housing and operating large amounts of high-performance mining hardware. As in, customers got paid to use the electrical. The private key must always be kept secret and never shared with other people. Daily Herald. We're not dealing anymore with an isolated or distinct block of transactions, but rather with a chain of blocks that starts literally at the beginning of the entire Bitcoin. Due to the limited supply of computational power, miners litecoin to bitcoin stocks that own coinbase also incentivized not to cheat. Retrieved 26 July It is a type of asymmetric cryptography that is considered more efficient compared to classic RSA cryptography. Transaction records. Financial Crimes Enforcement Network.
The coding of the blockchain algorithm is set up to reward the person for doing the mining and thus helping to verify the blockchain transactions while keeping the network safe. The Economist wrote in that these criticisms are unfair, predominantly because the shady image may compel users to overlook the capabilities of the blockchain technology, but also due to the fact that the volatility of bitcoin is changing in time. Retrieved 2 February The signature of block 2 is now partially based on the signature of block 1, because it is included in the string of data in block 2. Retrieved 30 October To achieve independent verification of the chain of ownership each network node stores its own copy of the blockchain. Bitcoin mining is done by specialized computers. This signature is now added to the data of block 2. Certainly the possibily of enabling such exciting and potentially transformative technologies is worth the energy cost… particularly given the synergy between smart devices and power saving through increased efficiency. Bitcoin scalability problem. The longer it takes to actually come up with a proof that works with respect to a given challenge. Securities and Exchange Commission's Division of Trading and Markets, had identified several manipulation techniques of concern in March Bitcoin Gold changes the proof-of-work algorithm used in mining, as the developers felt that mining had become too specialized. Griffin and Amin Shams in suggests that trading associated with increases in the amount of the Tether cryptocurrency and associated trading at the Bitfinex exchange account for about half of the price increase in bitcoin in late The hash function makes it impossible to predict what the output will be. You need to use the software to point your hash rate at the pool. An extremely rare example recently occurred on block , Creating a bitcoin address requires nothing more than picking a random valid private key and computing the corresponding bitcoin address. Financial Industry Regulatory Authority.
After all, it requires the majority of the computational power to create the longest version of the blockchain. This is something we're asked everyday! The coding of the blockchain algorithm is set crypto future what exchange can you short cryptocurrencies to reward the person for doing the mining and thus helping to verify the blockchain transactions while keeping the network safe. Retrieved 5 September For a general introduction the history of cryptography please check out our previous blog post buy and sell bitcoin using paypal coupons for bitstamp. One node will send information to a few nodes that it knows, who will relay the information to nodes that they know. The only way that an alteration can stay undetected, is if all the blocks stay chained to each. That is the amount of time that the bitcoin developers think is necessary for a steady and diminishing flow of new coins until the maximum number of 21 million is reached expected some time in Retrieved 27 April Retrieved 9 December Though transaction fees are optional, miners can choose which transactions to process and prioritize those that pay higher fees. Red may now consider sending the goods to Green. Archived from the original on 25 March In order to understand why, you will need to understand how the signatures are created. Cryptographic hash functions.
Retrieved 14 June Enterprising coders soon discovered they could get more hashing power from graphic cards and wrote mining software to allow this. The blockchain now looks like this:. There are many aspects and functions of Bitcoin mining and we'll go over them here. Zcash Zcoin. Retrieved from " https: Nakamoto is estimated to have mined one million bitcoins [28] before disappearing in , when he handed the network alert key and control of the code repository over to Gavin Andresen. Bitcoin Recruits Snap To". And let's say these four transactions have been broadcast out. Senate held a hearing on virtual currencies in November Moreover, the number of valid private keys is so vast that it is extremely unlikely someone will compute a key-pair that is already in use and has funds. By joining a mining pool you share your hash rate with the pool. The only downside for home miners is that mining rigs are often noisy and un-anaesthetically-pleasing devices. As discussed previously in step 3, altering a block will unchain it from the subsequent blocks. By guessing at random. It's 'the Harlem Shake of currency ' ".
The signature that corresponds with this new set of data is no longer X Archived from the original on 9 April Retrieved 23 May Archived PDF from the original on 6 November The Washington Post. Subscribe Here! Articles containing potentially dated statements from All articles containing potentially dated statements Cex.io temporarily suspends cloud mining services cgminer usb block erupter German-language sources de CS1: Archived from the original PDF on 28 December Retrieved 2 November Archived from the original on 23 February The fewer zeroes that you require, the less time it will. Green sends 1 bitcoin to Red. These documents are the blocks of data.
Also get to collect the transaction fees that were specified in the transaction records. Lovink, Geert ed. The Bitcoin software has different levels of security and tradeoffs in order to verify the blockchain. Power companies paid their customers to use more power so that the energy could be safely dispersed. During its 30 months of existence, beginning in February , Silk Road exclusively accepted bitcoins as payment, transacting 9. The second biggest Ponzi scheme in history". Bloomberg LP. Bitcoin is different. This allows bitcoin software to determine when a particular bitcoin was spent, which is needed to prevent double-spending. In a more concrete example, this can be used to take a sequence of letters of any length as input — what we call a string — and return a sequence of letters of a fixed length. By joining a mining pool you share your hash rate with the pool. A brass token with credentials usable to redeem bitcoins hidden beneath a tamper-evident security hologram.
For broader coverage of this topic, see Cryptocurrency wallet. It is considered impossible anyway though, and here is why:. Retrieved 9 January Distributed hash power spread among many different miners keeps Bitcoin secure and safe. Number of bitcoin transactions per month logarithmic scale [74]. Hidden categories: Authorities will bring down 'hammer' on bitcoin". Get Bitcoin Mining Software Bitcoin mining software is how you actually hook your mining hardware into your desired mining pool. Bitcoin software Alternative currencies Application layer protocols Computer-related introductions in Cryptocurrencies Currencies introduced in Digital currencies. For the first time we have a system that allows for convenient digital transfers in a decentralized, trust-free and tamper-proof way. Ethereum Ethereum Classic. Financial News.
Archived from the original on 27 February You can picture it like this:. European Banking Authority. Category Commons List. The data in block 1 is now linked to block 2 by adding the signature of block 1 to the data of block 2. Buy Bitcoin Worldwide does not offer legal advice. New York Times. How many bitcoin are there and when will the popular crypto token run out? Archived from the original on 10 July Congrats on still being here! Whenever a new block is mined, that miner how to buy a whole individual bitcoin in one purchase bitcoins available now rewarded with some currency block reward, transaction fees and thus are incentivized to keep mining.
Retrieved 10 April Retrieved 10 January A network of communicating nodes running bitcoin software maintains the blockchain. As you can see, the hash signature of this block and the hash of the previous block both start with a number of zeroes. To make the best use of this documentation, you may want to install the current version of Bitcoin Core, either from source or from a pre-compiled executable. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Retrieved 20 December Oxford Business Law Blog. The unit of account of the bitcoin system is a bitcoin. The Commodity Futures Trading Commission then subpoenaed the data from the exchanges. Following the first delivery date in January , the CME requested extensive detailed trading information but several of the exchanges refused to provide it and later provided only limited data. The block size limit of one megabyte was introduced by Satoshi Nakamoto in This signature is now added to the data of block 2. You will earn less than one penny per year and will waste money on electricity. Follow-up articles are right below. Now imagine if the data in block 1 is altered.
TheVerge News. A transaction fee is like ethereum chart australia litecoin mined coin maturation time tip or gratuity left for the miner. And in fact, every transaction block as I mentioned just now incorporates the previous transaction lock. Step 2: And they're going to incorporate any new unincorporated transactions into that new transaction blocking. In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. The use of bitcoin by criminals has attracted the attention of financial regulators, legislative bodies, law enforcement, and the media. AOL inc. Without proper rendering supportyou may see question marks, boxes, or other symbols. Retrieved 13 September It is the new money of the internet. The Bitcoin software has different levels of security and tradeoffs in order to verify the blockchain.
Economists define money as a store of value , a medium of exchange , and a unit of account. How do they find this number? Namespaces Article Talk. Authored by Noelle Acheson. Retrieved 8 November All right, now once this proof of work is found, let's say that the proof of work is eventually found. Now you may get some word discrepancies because of network latency issues and so on. Retrieved 20 September